Notice of Security Incident
What Happened? Following a successful phishing effort on 11 Feb 2020, a security incident occurred when criminals gained access to a Gate 15 email account for approximately 15 hours.
Notable Findings.
- The phish was initiated for purposes of attempting Business Email Compromise (BEC).
- Within one hour of gaining access, the criminals used Office 365 capabilities to run an automated search to scan for potential targets – organizations that may be involved in invoice transactions.
- Two targets were identified and within one hour, a well-written BEC attempt was launched upon one of those potential targets. The other identified target was, one, not a viable target, and, two, not engaged by the criminals. A redacted version of the sent message follows.
Hi [REDACTED],
I do have a request for you. We are currently looking at closing our account with [REDACTED] due to the fees charged with receiving payments.
Is there any possibility of your AP department issuing direct payment to our bank account without passing through [REDACTED]?
Please advise.
Thank you for your assistance.
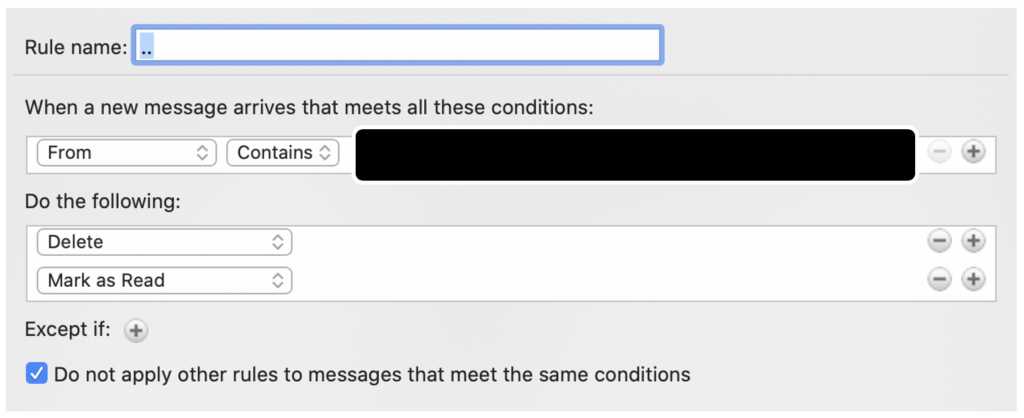
- In addition to the quickly delivered BEC message, criminals modified and added rules in the user’s Office 365 account to mark messages from the targeted organization as read and to delete responses from the targeted organization.
- Upon losing access to the account the following morning, there was an observable increase in phishing attempts to the same account in subsequent days, as well as other outreach suspected to be from the same actor(s).
- The BEC was unsuccessful.
Potential Concerns.
- The individual(s) involved in this criminal activity seemingly had a very specific focus (BEC) and it is not known that other nefarious activity was conducted.
- At this point, there is no observed evidence that other criminal mischief has been conducted.
- It is not known if other contact information was accessed by the criminals and we have seen no evidence that it was.
- Nonetheless, out of an abundance of caution, please be cautious opening links and attachments and verify that the “from” address is correct. This incident could enable follow-on phishing attempts seeking to emulate Gate 15 accounts.
Our Response.
- Within approximately 15 hours of the suspected compromise, the password to the account was changed, denying further abuse.
- Clients have been notified of the compromise directly.
- Passive notification has been included in the signature block of the compromised account.
- Gate 15 personnel are being briefed on additional details.
- We are moving towards implementation of a simple solution that would have prevented the compromise. As recently reported in ZDNet, “Speaking at the RSA security conference last week, Microsoft engineers said that 99.9% of the compromised accounts they track every month don’t use multi-factor authentication, a solution that stops most automated account attacks.” The value of two-step, two-factor or multi-factor authentication is well understood and appreciated by our team, yet, for a variety of reasons, had not yet been implemented in the one place where it is probably most important – our email. We are taking action to correct this and regret that it was not already in place.
More Information. You may contact us in writing at gate15@gate15.global or you can call us at 571.510.0985. On behalf of our team, we regret any inconvenience this may cause you.
Sincerely,
Andy Jabbour
Co-Founder and Managing Director
(also, the guy who was phished)
Gate 15


