By Alec Davison, Gate 15 Junior Risk Analyst
Just as businesses depend on email to conduct their day-to-day operations, threat actors count on it for conducting malicious activity. Year-after-year email remains one of the top attack vectors through which adversaries are able to gain access to and compromise an organization’s network infrastructure, primarily via phishing attacks. Indeed, according to Proofpoint, in 2021, 83 percent of organizations surveyed said they experienced at least one successful email-based phishing attack. Successful phishing attacks can lead to the loss of sensitive data, stolen account credentials, financial loss, and the deployment of malware such as ransomware.
In order to defend against a threat, it’s important to understand it, because knowing is half the battle.

Phishing is a type of cyber attack where malicious actors send messages pretending to be a trusted individual or organization. “Phishing messages manipulate a user, causing them to perform actions like installing a malicious file, clicking a malicious link, or divulging sensitive information such as access credentials,” according to Checkpoint. Phishing is also the most common form of social engineering, which involves employing deception to manipulate or trick a user into performing some type of action. Moreover, phishing attacks are not only one of the most common and enduring cybersecurity threats, but they are also evolving as threat actors devise more ways to successfully compromise individuals and entities. In fact, some of the most common subsets of phishing include spear phishing, vishing, url phishing, and whaling, among others.
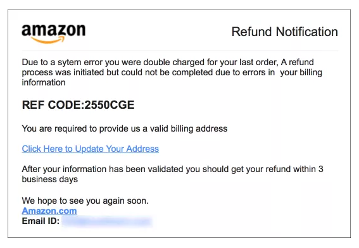
One of the most common forms of phishing, spray phishing, involves an adversary impersonating a trusted third-party, such as Microsoft or Amazon, and sending mass emails out to hundreds or thousands of individuals either with malware links or attachments or asking for an individual to reply back and divulge sensitive information. A more sophisticated form of phishing is known as spear phishing, it is much more targeted and involves social engineering tactics. In this attack method, an adversary conducts research on a particular entity or individual and uses specific lures that would seem relevant to the individual receiving the email and thus making it more likely to fool the potential victim. For instance, a threat actor might send an email posing as an employee referring to a product or event they are working on and then asking their boss or colleague to grant them access to a certain account or to open an attachment that appear relevant to what they may be working on. These targeted spear phishing attacks are on the rise and are likely to evolve as threat actors look for new ways to compromise and infect our systems.
Nevertheless, despite the growing threat, there are a number of steps organizations can take to protect themselves against phishing attacks. Of course, there is email security software available to help weed out phishing emails from legitimate ones. But the most important action organizations can take is implementing user awareness training. Frequent, understandable awareness training is one of the best tools we have available to keep our organizations safe and secure. User awareness training is critical for fostering a disciplined and informed workforce that can carefully discern legitimate email communications from phishing scams. Its critical that employees carefully screen suspicious emails, look out for red flags, and user another means of communication to verify the legitimacy of the message. Awareness training should occur regularly and stress the importance that employees should “think before you click.”
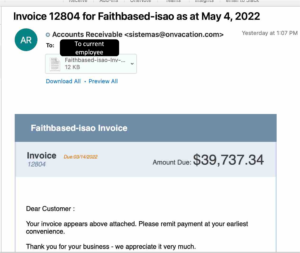
Here at Gate 15, we also encounter phishing attacks on a day-to-day basis (two examples of phishing attacks we received our posted below). As part of our security culture, Gate 15 employees regularly take screenshots of phishing emails we receive and we share them with the rest of our team so that we are all aware of the potential types of threats we may encounter, while also helping foster greater security awareness and cyber best practices amongst our team. Many times, multiple team members are able to quickly confirm that they too have received the same phish. Of course, some of the phishing emails we receive are more sophisticated than others.
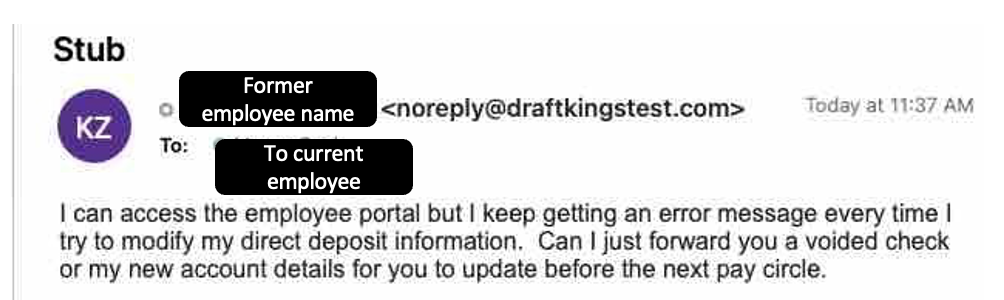
One of the most recent phishing attacks sent to an employee involved a threat actor impersonating a former employee claiming they had trouble accessing their financial information associated with our company and asked to have their payment information updated by one of our employees.
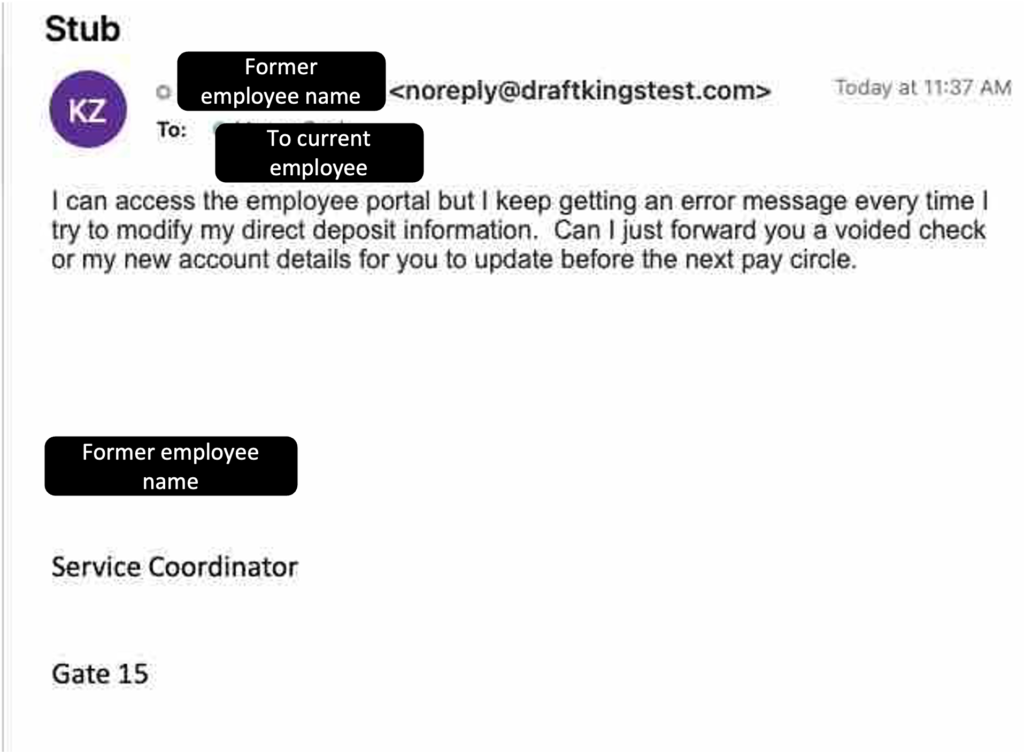
Luckily, the employee flagged the suspicious email before divulging any information or clicking on malicious links. But this specific spear phishing incident involved sophisticated social engineering techniques, which is often the primary factor that entices individuals to perform an action thereby rendering the phishing attack a success and comprising their device or network. Consequently, as noted above, fostering a security culture that encourages skeptical employees who carefully screen emails and regularly conduct awareness training is key to keeping you and your organization secure against this growing threat.
Understand the Threats.
Assess the Risks.
Take Action.
Understand the threats! Subscribe to our free daily paper and subscribe to our podcasts!
Take action! Our team specializes in intelligence and analysis, preparedness activities to include the development of plans, training, and exercises, and we can help you build the relationships and capabilities you need for effective information sharing operations to support your ability to prevent, protect against, mitigate, respond to, and recover from the threats and hazards that pose the greatest risk to your organization in our complex, all-hazards environment.