Taking this week’s reports in two parts, this blog takes a look at one of the notable realizations  to come out of the Dylann Roof trial. Informed by our daily reporting on the global, all-hazards threat environment, the Gate 15 Threat and Risk Analysis Cell (TRAC) focused in on the South Carolina trial in Wednesday’s Threat Dashboard writing, “Last week, Dylann Roof, the shooter in the June 2015 shooting at a black church in South Carolina, was found guilty in the murder of nine church parishioners. During the trial, it was revealed that the shooter conducted extensive surveillance prior to the attack, visiting the church up to six times in the preceding months, as well as other historically black landmarks in the area. This type of activity is one element of the routine Attack Cycle used in hostile events, which includes ‘initial surveillance’ followed by periods of ‘intense surveillance’ once a target has been selected.”
to come out of the Dylann Roof trial. Informed by our daily reporting on the global, all-hazards threat environment, the Gate 15 Threat and Risk Analysis Cell (TRAC) focused in on the South Carolina trial in Wednesday’s Threat Dashboard writing, “Last week, Dylann Roof, the shooter in the June 2015 shooting at a black church in South Carolina, was found guilty in the murder of nine church parishioners. During the trial, it was revealed that the shooter conducted extensive surveillance prior to the attack, visiting the church up to six times in the preceding months, as well as other historically black landmarks in the area. This type of activity is one element of the routine Attack Cycle used in hostile events, which includes ‘initial surveillance’ followed by periods of ‘intense surveillance’ once a target has been selected.”
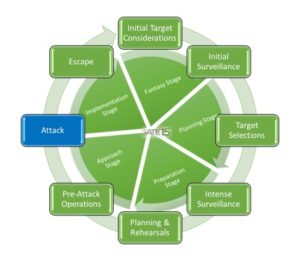 Elaborating on that in Thursday’s Torpedo Report, Dave Pounder added, “Preventing these types of lone actor attacks is difficult, especially with individuals who are isolated, or ostracized within their community, but there are common indicators of an individuals’ movement towards violent action that can be detected and provide opportunities to frustrate plots and prevent tragedy… Individuals planning an attack consistently follow a routine attack cycle, which repeatedly exposes them up to detection and disruption. While some attacks are thwarted at the “last second,” security personnel, supported by a trained and aware workforce, have the opportunity to detect and interdict plots before they reach the attack phase. Leaders should emphasize identifying attackers early in the process, before an attack is conducted. An alert and aware staff can take the proper actions to prevent workplace disasters, as recently occurred in the Washington DC area.
Elaborating on that in Thursday’s Torpedo Report, Dave Pounder added, “Preventing these types of lone actor attacks is difficult, especially with individuals who are isolated, or ostracized within their community, but there are common indicators of an individuals’ movement towards violent action that can be detected and provide opportunities to frustrate plots and prevent tragedy… Individuals planning an attack consistently follow a routine attack cycle, which repeatedly exposes them up to detection and disruption. While some attacks are thwarted at the “last second,” security personnel, supported by a trained and aware workforce, have the opportunity to detect and interdict plots before they reach the attack phase. Leaders should emphasize identifying attackers early in the process, before an attack is conducted. An alert and aware staff can take the proper actions to prevent workplace disasters, as recently occurred in the Washington DC area.
“Disrupting the attack cycle as early as possible is critical. In addition to traditional physical security concerns and indicators, attackers will continue to increasingly exploit technology to lower their profile and seek to improve their chances for success. The Mirai Botnet recently took control over hundreds of thousands of unsecure IoT devices to conduct DDoS attacks against high volume websites. This could potentially be modified to frustrate network defenses in advance of a physical attack. Hackers have also been known to tap into baby monitors and IP cameras and take control over the camera and terrorist groups and other hostile actors these techniques and related references (such as the ‘Book of Terror‘) to aid in their surveillance periods to limit their physical presence near a target while still gaining valuable information.”
 We’ll soon be sharing more information regarding our Hostile Events Preparedness Series (HEPS), providing organizations a complete preparedness solution to addressing the threat of a hostile event. We use the term “Hostile Event” to encompass a variety of events involving the killing or attempt to kill in public while having access to additional victims. This includes active shooter incidents, workplace violence and workplace attacks, lone actor and low-tech terrorism, complex coordinated terrorist attacks, and other related activities. Working with premier partners to ensure the most complete and expert support, HEPS will be able to help organizations mitigate the risks associated with a potential Hostile Event to protect your people, property and interests.
We’ll soon be sharing more information regarding our Hostile Events Preparedness Series (HEPS), providing organizations a complete preparedness solution to addressing the threat of a hostile event. We use the term “Hostile Event” to encompass a variety of events involving the killing or attempt to kill in public while having access to additional victims. This includes active shooter incidents, workplace violence and workplace attacks, lone actor and low-tech terrorism, complex coordinated terrorist attacks, and other related activities. Working with premier partners to ensure the most complete and expert support, HEPS will be able to help organizations mitigate the risks associated with a potential Hostile Event to protect your people, property and interests.
The complete Torpedo Report includes additional background and analysis as well as some preparedness and operational ideas for leaders to consider. This week’s reports and previous releases can be linked to from the “Reports” tab of this website.
 To help leaders maintain active threat situational awareness, we distribute our (free!) daily paper and the above mentioned weekly products. Our team hopes they can help you achieve a sound background as you assess your organizational risks and then apply a threat-informed, risk-based and prioritized approach to preparedness and operations. If you’re not already signed-up, subscribe to our free products and receive them directly! Free reports include our daily paper, the Gate 15 SUN, with additional detail, focus and analysis in the weekly Threat Dashboard and Torpedo Report.
To help leaders maintain active threat situational awareness, we distribute our (free!) daily paper and the above mentioned weekly products. Our team hopes they can help you achieve a sound background as you assess your organizational risks and then apply a threat-informed, risk-based and prioritized approach to preparedness and operations. If you’re not already signed-up, subscribe to our free products and receive them directly! Free reports include our daily paper, the Gate 15 SUN, with additional detail, focus and analysis in the weekly Threat Dashboard and Torpedo Report.
Follow our Gate 15 team on Twitter: @Gate_15_Analyst; and our Gate 15 page on LinkedIn and subscribe to our free daily and weekly products!



