By Evan Pounder
As we continue to develop more advanced and effective approaches to combat attacks made by threat actors, it becomes increasingly more important to identify new and evolving trends that malicious groups utilize to create fear, panic, disruption, and destruction. It is not breaking news that our world continues to transition into a more digital atmosphere, and as a result of the COVID-19 pandemic, maybe progressing at an even more accelerated rate. As with any type of advancement, there come new and emerging threats that malicious actors attempt to use to take advantage of weaknesses that have yet to be discovered. These new strategies that are being used may attempt to infiltrate the cyber barriers of different organizations, but they can create real physical dangers to people across the globe.
One of the most recent approaches that threat actors have begun to implement goes by the name telephony denial of service (TDoS) attacks. WeLiveSecurity describes the goal of these attacks as “to overwhelm a telephone system to such an extent that it would be unavailable for the intended user.” While this might not seem incredibly harmful at a foundational level, these barrages can create absolute chaos and manifest immense amounts of physical damage when implemented strategically. Automated TDoS attacks could potentially target emergency call centers, berating them with false calls for extended periods, a practice that could potentially delay the emergency response by extended time frames. Pair one of these attacks on an emergency service center with a physical attack, and there could be an exaggerated amount of damage caused as these centers scramble to decipher which calls coming in are authentic, and which ones are distractions. This type of attack has even caught the eye of the Federal Bureau of Investigation (FBI) as they have issued a blunt warning about the dangers of TDoS attacks.

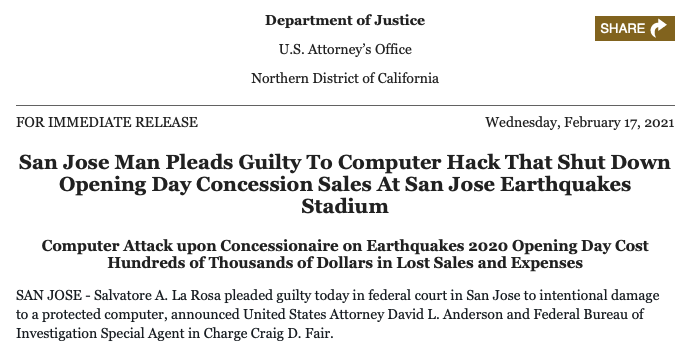
Another type of threat that has pushed itself into the front of the crowd comes in the form of a blended threat that originated from insider intrusions. The Department of Justice (DOJ) has recently published an example of this threat coming in the form of an ex-employee of Spectra Food Services and Hospitality, which controls the online concessions management account for San Jose Earthquakes (Major League Soccer). This former employee created an unauthorized intrusion into the stadium’s administrative port from his own residence and using a password to access the Spectra concession menu and payment selection. This intrusion ultimately resulted in a complete shutdown of the system, creating an estimated $268,000 in damages. Although this attack occurred on a rather nonessential organization and did not result in any physical harm or damages apart from financial costs, it does showcase the problem of insider threats against organizations. For example, an attack like this against an organization’s security or access controls could enable a much more dangerous physical threat. As security systems become more and more complex and integrated, threat actors have begun to more heavily rely on people within the institution that make an intrusion like this one more feasible. Thus, it has become even more increasingly important that organizations be prepared and train against insider threats.
While these two types of blended threats certainly do not account for a majority of the possible threats against organizations, they do illustrate the importance of remaining vigilant against new and emerging strategies, tactics, and techniques that threat actors may use. Malicious groups are constantly developing new approaches to create as much panic and damage as they can, and one of the major ways organizations can fall victim to newly developed approaches is by remaining complacent in their current security strategy and not evolving with the threat. Institutions must continue to adapt to changing procedures and new technology, as well as look for gaps in their own security before threat actors have a chance to exploit them.
Understand the Threats.
Assess the Risks.
Take Action.
Understand the threats! Subscribe to our free daily paper and subscribe to our podcasts!
Take action! Our team is here to help you build the relationships and capabilities you need and to assist in the development of plans, training, and exercises to support your ability to prevent, protect against, mitigate, respond to, and recover from the threats and hazards that pose the greatest risk to your organization in our complex, all-hazards environment.
Evan Pounder is an intern at Gate 15. He is a third year Army ROTC cadet at the University of South Carolina majoring in finance, with minors in French and Military Science.
