Access the Gate 15 White Paper on The Hostile Event Attack Cycle (HEAC), 2021 Update, via the link below.
Excerpt follows.
White Paper: The Hostile Event Attack Cycle (HEAC), 2021 Update
Developed by David Pounder and Andy Jabbour, Gate 15, with an introduction by Rob Yandow.
“A basic understanding of the Hostile Events Attack Cycle (HEAC) is a critical element in the development of a functional and effective plan to prepare for, and perhaps prevent, a hostile attack against an individual, group, or physical facility. This white paper, as presented by Gate 15, provides an excellent analysis of the various components of the HEAC by identifying and describing each stage of the Cycle along with the progressive steps that attackers could take in furtherance of their goal which is to perpetrate violence against their selected target(s). The paper also identifies the important connection between the Hostile Events Attack Cycle and the Pathway to Violence. I will undoubtedly incorporate the information contained in this white paper into future safety and security discussions at all levels.”
Rob Yandow, Retired Police Captain, National Sector Chief, InfraGard Emergency Services Sector
The Hostile Event Attack Cycle (HEAC), 2021 Update.
Looking across the threat spectrum, hostile events can take the form of many types and their impacts on individuals, organizations, and community can be far-reaching, and, in a lot of ways, devastating. They can incorporate many different types of threats. These include[1] active shooter incidents, workplace violence and workplace attacks, lone actor and low-tech terrorism, complex coordinated terrorist attacks, fire as a weapon, weapons of mass destruction, and other related hostile actions. And they are characterized by several factors, and employed through a variety of means, weapons, and tactics used to cause physical injury or death. Regardless of the attack method, hostile events present an operational range of hazards requiring a more complex response strategy that blurs the lines between traditional law enforcement, fire, and emergency medical service (EMS) duties and responsibilities. Whether they realize it or not, threat actors go through a cycle for planning and executing an attack. This process is defined as the Hostile Event Attack Cycle, or HEAC, and it is based on a review of various attacks, as well as other articles based on various types of attack processes.
The purpose of this paper is to provide an understanding of the HEAC which can help organizations prepare for various threat courses of actions and develop enhanced security measures as necessary to potentially disrupt threat actors’ planning and to enable the organization to be prepared to respond appropriately.
In early 2016, The Gate 15 Company (Gate 15) consolidated several existing concepts and developed the HEAC model. This was shared amongst information sharing and analytical communities, and other security professionals, and subsequently informed the basis of Gate 15’s hostile events preparedness program (the Hostile Events Preparedness Series [HEPS]). Initially eight phases, this level of understanding about the threat and their planning process provided insight to organizations to potentially counter threat activities and reduce the risk to their organization. However, as more attacks were analyzed, some consolidation to the HEAC has occurred. While the actions within the phases are distinct, there are instances in which actions bleed together and do not necessarily follow a chronological order. Additionally, with the abundance of information available to threat actors online and through social media platforms, threat activities can be expeditated and done in conjunction with physical activities.
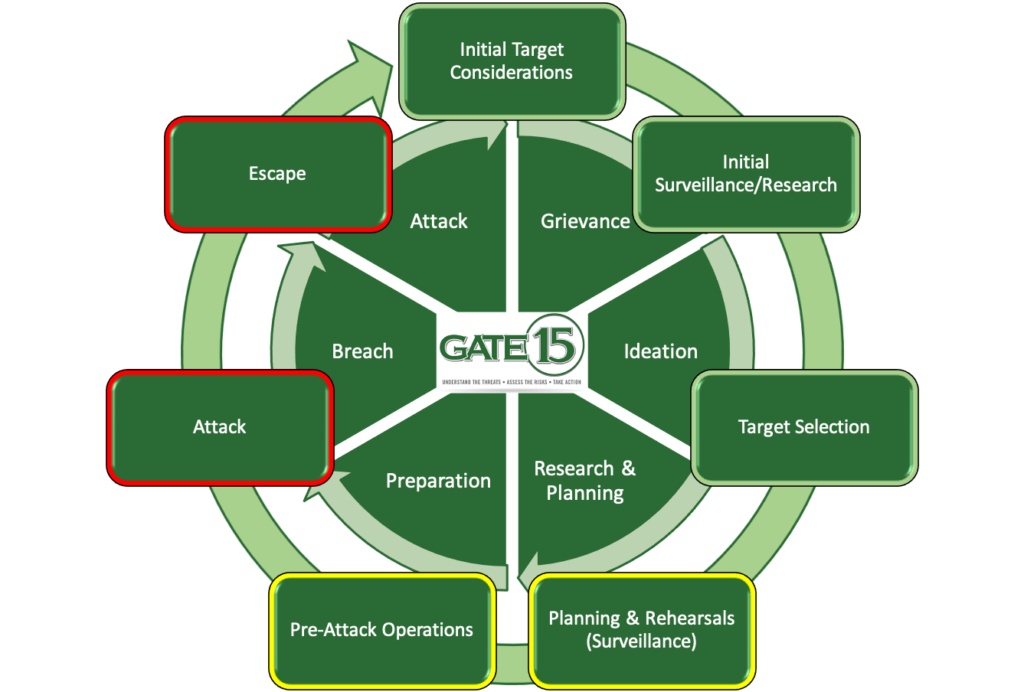
They HEAC process merges several important concepts and publications from within the public and private sector.
- At the foundation is a basis developed through observed active shooter instances[4] which include five distinct stages: Fantasy; Planning; Preparation; Approach; and Implementation.
- The individual elements which include the outer and inner blocks of the cycle correspond to the Pathway to Violence[5]and FBI[6] information and analysis which incorporate Grievance, Ideation, Planning and Research, Breach, and Attack.
- As a result, HEAC can be viewed as seven phases, represented in the chart below.
By utilizing this process, threat actors have a framework, again whether followed consciously or not, in which they select the best target to satisfy their purpose; that they have the right supplies and equipment; and then once the attack is over, that they conclude the attack as intended – via an escape or death. Whether it is a physical attack designed to inflict mass casualties, or an attack on facilities or infrastructure, the HEAC is consistently followed as threat actors plan, prepare, and execute their attacks.
A couple points to consider in reading this report:
- The term threat actor used throughout this document applies to an individual or group.
- When evaluating hostile events, we make a clear distinction between these events (as defined above) and crimes of passion, in which an act is committed against another because of sudden strong impulse such as sudden rage, rather than as a premeditated crime. Hostile Events discussed in this report may be conceived based on a grievance but are not impulse driven; they are not spur of the moment decisions. This does not discount that the impulse or source of that impulse does not factor into the target selection, but it is not the sole factor in committing the act.
- In a similar vein to the above, the hostile events described through the HEAC are different from other criminal incidents that may be called active shooter incidents but in fact related to criminal violence, or other type of activity such as gang-related, or narcotics incidents.
