By Andy Jabbour
This is an update to the original post, “Terminology for $500. What Are Blended Attacks?” 26 May 2017, and the update, “Blended Threats: Understanding an Evolving Threat Environment,” 24 Jan 2018. As our team continues projects focused on the Blended Threat environment, we have determined further clarification is needed in the definition provided below. That is incorporated into this update.
Last May, with the generous input of colleagues, we posted a blog titled, “Terminology for $500. What Are Blended Attacks?” At that time, the world was coming out of the WannaCry ransomware outbreak and that had me thinking on an effective way to capture the idea of cyber incidents with physical impacts. If you don’t want to read that post, the skinny of it is that we arrived to this:
Blended Attack. A Blended Attack is deliberate, aggressive action that causes harm to both cyber and physical systems.
But, now, eight months or so on and with time to further reflect on the current and evolving threat environment – and with some great perspective from my teammates, colleagues and the communities we get to contribute to, I realize that there needs to be a broader term, which my teammates and I have found ourselves using already in numerous efforts in everything from addressing Internet of Things (IoT) threats to observed attacks such as Triton (FireEye) / Trisis (Dragos) malware (which Dragos described as “malware that was developed and deployed to at 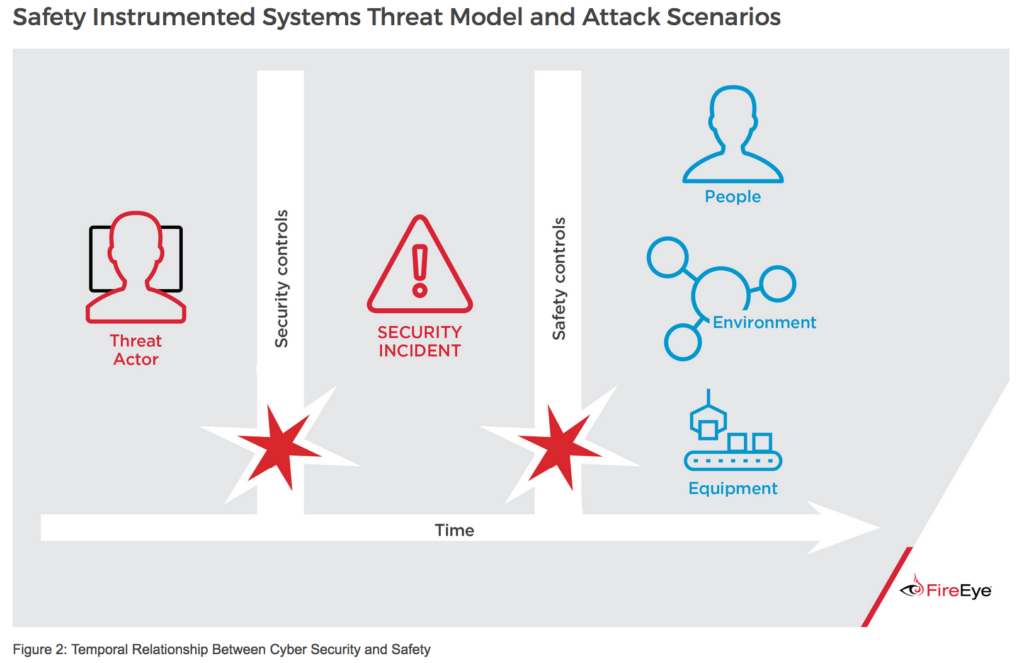 least one victim in the Middle East to target safety instrumented systems”) and an array of threats and incidents not necessarily limited to “deliberate, aggressive action.” So, Houston, we have a problem, and I’m not talking about losing Mike Vrabel to the Titans… What do we call cyber-physical threats that are not necessarily attacks, or deliberate?
least one victim in the Middle East to target safety instrumented systems”) and an array of threats and incidents not necessarily limited to “deliberate, aggressive action.” So, Houston, we have a problem, and I’m not talking about losing Mike Vrabel to the Titans… What do we call cyber-physical threats that are not necessarily attacks, or deliberate?
Think of the many exposures our rapidly increasingly connected world has to not just blended attacks, but blended threats, where cyber and physical systems are potentially exposed and at risk. We need a clear and understandable way to address such threats. The 2010 DHS Risk Lexicon provides two important definitions that are good to know and useful to this idea – definitions for Threat and Risk.
- Threat: A natural or man-made occurrence, individual, entity, or action that has or indicates the potential to harm life, information, operations, the environment, and/or property.
- Risk: Potential for an unwanted outcome resulting from an incident, event, or occurrence, as determined by its likelihood and the associated consequences
Those are very sound definitions. The point of specifying the type of threat is simply to be able to provide more precise understanding, as we would if we are differentiating between, say a flood threat or the threat of an active shooter.
For purposes of having a term we can use to describe those cyber and physical threats mentioned above, our team has been using the term “Blended Threat.” A Blended Threat is a natural, accidental, or purposeful physical or cyber danger that has or indicates the potential to have crossover impacts and harm life, information, operations, the environment, and/or property.
A Blended Threat is a natural, accidental, or purposeful physical or cyber danger that has or indicates the potential to have crossover impacts and harm life, information, operations, the environment, and/or property.
How present are such blended threats? Returning to the idea of blended attacks, consider a cyberattack on a facility – from a hospital to a Fortune 500 corporate headquarters – where physical systems are compromised, with so many networked systems that could potentially be effected. In the case of Trident, the malware was deliberately deployed to manipulate emergency shutdown capabilities. Following observed attacks on energy facilities – such as in Ukraine, the potential for seriously consequential cyber-physical attacks on critical infrastructure, to include critical lifelines, is not just theoretical, but a real threat. While such capabilities may be initially limited to robust nation-states, history has shown that there is possibly nowhere that the idea of trickle-down economics has proven more real than in cybercrime, where what is once limited to a few eventually is employed by even unsophisticated threat actors. Whether by an inadvertent post (i.e., “Trisis has mistakenly been released on the open internet”) or an insider threat or hacking (such as the NSA enjoyed…), dangerous capabilities developed by the few seem to get into the hands of the many, potentially exposing physical systems to cyber threats by an increasing number of characters.

But, its not just the cyber initiated attack that is a concern. What about a hostile event – a terrorist or other extremist attack – that impacts computer systems and networks? From the office to the data center, physical attacks can have cyber impacts. And it needn’t be an attack at all. What if vital systems are compromised in a flood or due to a major physical disruption to communications or energy? While perhaps less likely, in an increasingly connected world, the threats to cyber-physical systems can’t be thought of as unidirectional from cyber to physical.
So, it isn’t just blended attacks we need to think of. We need to be cognizant of, and prepared for, a wide array of Blended Threats that can impact organizations (and our homes…) directly and indirectly via third-parties, supply chain dependencies, critical lifelines and nearly everything that touches our organization. As the threat environment changes, the risks organizations are facing also change. Some threats may not have realistically significant enough organizational risk today to make them priorities. But leaders need to look past the immediate risks of today and also consider the emerging threats and anticipated risks and how those will impact the organization as new purchases, locations, personnel, operations and other variables perhaps change some of those risk assessments.
In an increasingly connected world, the threats to cyber-physical systems can’t be thought of as unidirectional from cyber to physical.
Will increasing deployment of IoT devices impact your risk? Will a new facility in areas that are seeing increased wildfires or mudslides pose new challenges? Does your proximity next to higher risk targets have an associated risk to your organization? Do geopolitical events create reasons for international threats to target your organization or personnel, physically or their online presence? These aren’t just theoretical questions but questions based on situations and concerns organizations are experiencing right now.
This year, FEMA’s “National Level Exercise (NLE) 2018 will examine the ability of all levels of government, private industry, nongovernmental organizations, communities, and individuals to protect against, respond to, recover from, and implement continuity plans related to a major hurricane with localized catastrophic impacts… Recent real-world experience will help make NLE 2018 more realistic, more relevant, and help ensure we are well prepared for the 2018 Atlantic 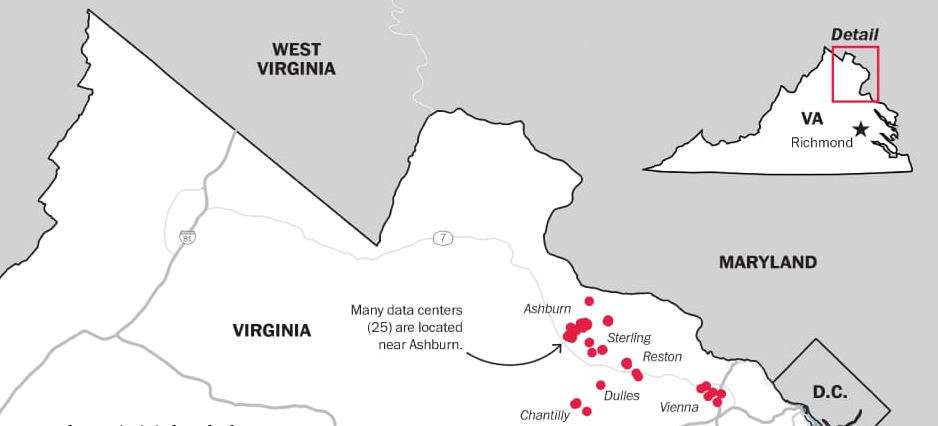 hurricane season.” Aside from the lessons learned through a remarkable 2017 hurricane season, what if “a major hurricane with localized catastrophic impacts” had effects into Northern Virginia’s data center cluster?
hurricane season.” Aside from the lessons learned through a remarkable 2017 hurricane season, what if “a major hurricane with localized catastrophic impacts” had effects into Northern Virginia’s data center cluster?
Right now, as Turkey, a nation the United States seems to be increasingly at odds with, is in a campaign against Kurdish forces in Syria. At the same time, actors believed to be associated with a Turkish hacker group are “targeting high-profile, verified Twitter accounts with the purpose of spreading Turkish political propaganda,” writes Christiaan Beek in a recent McAfee blog.
Geopolitical events may drive some to online antics and cyberattacks. But such activity needn’t be limited to international combat and political disputes. Hacktivism isn’t limited to social media takeovers and website defacements, and ransomware is pointing to much more impactful, physical impacts. Last year’s WannaCry outbreak impacted, “Almost 50 NHS Trusts (which) were hit by the… cyber-attack that left infected computers with encrypted files and at least temporarily unusable in many areas of the health service. The outbreak led to operations and appointments being cancelled or postponed.” But Stuxnet showed far greater potential physical consequences from cyberattacks, as does the more recent Triton attack.
Blended attacks are a reality, and as our once largely separate physical and cyber systems increasingly converge, Blended Threats are a real threat organizations need to be aware of, and plan for. Understand the Threats. Assess the Risks. Take Action.
This blog was written by Andy Jabbour, Gate 15’s Co-Founder and Managing Director. Andy leads Gate 15’s risk management and critical infrastructure operations with focus on Information Sharing, Threat Analysis, Operational Support & Preparedness Activities (Planning, Training & Exercise). Andy has years of experience working with partners across the critical infrastructure and homeland security enterprise to support national security and client business needs.
Maintain security and threat awareness via Gate 15’s free daily paper, the Gate 15 SUN and learn more about Hostile Events Preparedness and our HEPS Program here. Gate 15 provides intelligence and threat information to inform
 routine situational awareness, preparedness planning, and to penetrate the decision-making cycle to help inform time-sensitive decisions effecting operations, security, and resources. We provide clients with routine cyber and physical security products tailored to the individual client’s interests. Such products include relevant analysis, assessments, and mitigation strategies on a variety of topics.
routine situational awareness, preparedness planning, and to penetrate the decision-making cycle to help inform time-sensitive decisions effecting operations, security, and resources. We provide clients with routine cyber and physical security products tailored to the individual client’s interests. Such products include relevant analysis, assessments, and mitigation strategies on a variety of topics.
“Safety Instrumented Systems Threat Model and Attack Scenarios” via FireEye, “Attackers Deploy New ICS Attack Framework ‘TRITON’ and Cause Operational Disruption to Critical Infrastructure,” 14 Dec 2017, https://www.fireeye.com/blog/threat-research/2017/12/attackers-deploy-new-ics-attack-framework-triton.html
Infrastructure image, “The history of Triconex,” via Schneider Electric, https://www.schneider-electric.com/en/brands/triconex/triconex-history.jsp
Northern Virginia Data Center graphic via the Washington Post, “Northern Virginia, center of the (data) world,” 05 Jul 2017, https://www.washingtonpost.com/apps/g/page/lifestyle/northern-virginia-center-of-the-data-world/2226/
