By Brett Zupan
There is a tremendous amount of information that analysts, security and risk leaders, executives, and others try to process daily. In the abundance of noise, we strive to promote a simple idea to developing a threat-informed, risk-based approach to analysis, preparedness and operations: Understand the Threats, Assess the Risks, Take Action. That’s why it’s exciting to see REN-ISAC adopt a similar approach as it expands its offerings to bolster the higher education community’s security – both cyber and physical.
In Brief:
- The Research and Education Networking Information Sharing and Analysis Center (REN-ISAC) is continuously monitoring and assessing the threats that higher education faces.
- The higher education community faces a complex array of security risks from a variety of threat actors, due to the broad amount of educational opportunities colleges and universities offer. Those outside the community might be unaware of the number of actors, or how they have grown over recent decades.
- In an effort to increase higher education’s capacity to respond to cyber, physical, and blended threats, REN-ISAC is improving and increasing the services it offers to members. This includes targeted expansion of its trusted communication channels, a peer assessment program, and a multi-part blended threat exercise series across the United States to allow members to interact with each other and discuss security issues, best practices, and other topics in order to strengthen the community’s overall resilience.
The sophisticated cyber actors that universities face are some of the most developed espionage agencies in the world… This category is currently the most advanced threat that the higher education community faces, against global adversaries who use cutting edge tactics and tools.
Over the past year, reading the news might give the impression of a higher education community primarily consumed with the twin threats of on-campus protests and criminal hacking. However, in actuality, security professionals involved with this critical infrastructure community face a wide and complex array of all-hazards threats, including physical, cyber, and blended threats. The university campuses they protect function like miniature cities, offering a wide range of services to a diverse population – many of whom live on site – with all the security challenges that accompany such a setup. Schools that do not follow the traditional university campus model also require a broad security posture, as the facilities and materials required for higher learning are varied and have different security requirements. The purpose of this blog is to list the threats higher education is confronting, along with recent examples, in order to demonstrate this diversity to those outside of the community who want to gain a better understanding of what these institutions have to prepare themselves for. This community faces physical and cyber threats, from unsophisticated actors, sophisticated actors, and accidents/environmental factors. These factors combine to create the six categories this blog uses to sort the incidents that American university campuses have suffered in recent  years.
years.
Unsophisticated Physical Threats
There are many unsophisticated actors that threaten universities physically. At the base level, as a part of the background hum of crime expected on today’s society, university campuses are a target for criminals looking to take advantage of those on the premises. Student robberies are a common concern, as well as multiple types of firearm use and false bomb threats. Students, faculty, staff, and visitors are either victims or perpetrators in these incidents. For institutions located in a dense community, such as a university town or large city, events that occur nearby are under this umbrella. Violent events that occur nearby, such as armed robberies, can influence how a school sets its security posture. However higher education is at a uniquely higher risk of being targeted by student protests, acts of politically motivated violence/vandalism, or mass shootings. Student protests come from the communities that institutions serve and are typically non-violent in intent, while still aiming to disrupt the functions of the organization in a critical way. Due to their mission as centers of learning and discussion, more political protests occur when controversial speakers and similar contentious entities use the campus. These protests have become more violent in recent years, due to the increased political divide in America, as well as the rise of white supremacist propaganda seen in universities and the pushback that has occurred. While the deadly clashes seen in Charlottesville last year have been the most iconic manifestation of this trend, violent threats made to specific communities within the student population are also increasing. Finally, mass shootings remain a constant, yet unpredictable, threat that could come from students, staff, or outsiders.
Due to their mission as centers of learning and discussion, more political protests occur when controversial speakers and similar contentious entities use the campus.
Sophisticated Physical Threats
Sophisticated actors that threaten universities physically are, thankfully, rare. This category largely belongs to overseas terrorist groups who have had some experience in radicalizing and training American citizens and residents to conduct violence against soft targets. The only relevant incident approaching this category occurred in 2016, when a university student used a car and knife to attack a crowd on The Ohio State University’s campus. Prior social media posts linked the student to terrorist propaganda, though no communication was discovered with terrorist recruiters. 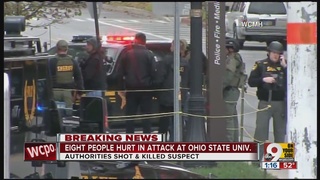 However, this event demonstrates how isolated university students from vulnerable communities on campus are at risk of being radicalized by these groups, and vulnerable universities campuses are at risk of being targeted. Despite some setbacks in recent years, the remnants of both the Islamic State and al-Qaeda continue to reach out to American communities and encourage attacks, whether by gun, knife, car, bomb, fire, or any other method these extremist organizations can come up with. What makes this threat more sophisticated than an average school shooting is the “technical support” provided to the actors by overseas handlers. Both al-Qaeda’s Inspire and the Islamic State’s Rumiyah magazines have contained advice on conducting terror attacks and after-action reports critiquing prior headline-grabbing attacks. Overseas handlers can use their battlefield experience to send similar advice customized to the type of attack a radicalized resident might carry out.
However, this event demonstrates how isolated university students from vulnerable communities on campus are at risk of being radicalized by these groups, and vulnerable universities campuses are at risk of being targeted. Despite some setbacks in recent years, the remnants of both the Islamic State and al-Qaeda continue to reach out to American communities and encourage attacks, whether by gun, knife, car, bomb, fire, or any other method these extremist organizations can come up with. What makes this threat more sophisticated than an average school shooting is the “technical support” provided to the actors by overseas handlers. Both al-Qaeda’s Inspire and the Islamic State’s Rumiyah magazines have contained advice on conducting terror attacks and after-action reports critiquing prior headline-grabbing attacks. Overseas handlers can use their battlefield experience to send similar advice customized to the type of attack a radicalized resident might carry out.
Accidental Physical Threats
Accidents and environmental factors can create physical consequences for university campuses. The best example of this threat is the false alarm. Institutions are facing an environment of heightened threat, where there is a lot of negative attention placed on an organization if they are perceived to have done less than everything necessary to protect its students and staff. This state of affairs, combined with the magnifying effect of social media, leads to halts on campus activity as security professionals track down false alarms. As miniature cities, universities are also prone to outbreaks of disease, which has physical impacts on security and potential blended and cascading threats and risks to cybersecurity and other operational activities. The spread of salmonella, norovirus, and other strains within the student body is a common occurrence that staff has to account for. Less broadly, due to the materials they handle, research institutions have to be concerned about the potential for hazardous accidents on site. Dangerous materials can be lost or improperly handled by students and faculty alike, leading to evacuations, damage to facilities, and health issues.
As miniature cities, universities are also prone to outbreaks of disease, which has physical impacts on security and potential blended and cascading threats and risks to cybersecurity and other operational activities.
Unsophisticated Cyber Threats
Unsophisticated cyber actors fall into two subcategories: criminal hackers and hacktivists. For similar reasons as protestors who physically threaten institutions, universities are popular targets for hacktivists. These hackers are typically less skilled. Some are ideologically invested in their message, some are associated with overseas governments or terrorist groups, and some are not fully invested in the hacks they conduct, simply doing them “for the lulz.” The defacement of a school’s web presence is a popular tactic , as well as collecting easily available information, such as student email addresses and passwords, to distribute to the media in order to fake a breach of the school’s network. Criminal hackers are subtler in comparison. The higher education community holds monetizable data, such as student financial information or health information, that can sell well online. Due to fast network speeds and a complex security environment for defenders, university networks are also common targets for attackers to take control of in order to hide attacks against other targets. Student emails, vulnerable servers, and unsecured devices are popular targets to compromise because they can either shield a criminal from being tracked or be sold to another criminal  interested in the same.
interested in the same.
Sophisticated Cyber Threats
In comparison, the sophisticated cyber actors that universities face are some of the most developed espionage agencies in the world. Research institutions produce valuable intellectual property and often work hand in hand with the American government to develop critically needed technologies. Economically, many cutting-edge and profitable commercial technologies are also incubated in this environment. In the last year, cyber espionage campaigns by China and Iran were unmasked, both targeting prominent universities in the West. Researchers from these universities typically work with their international colleagues and peers, creating a web of connections that allows state-sponsored hackers to target multiple countries easily. These espionage campaigns attacked this web, through targeted spear phishing and domain redirection, in order to access researchers’ machines and steal data that could be useful to their countries’ domestic industries. This category  is currently the most advanced threat that the higher education community faces, against global adversaries who use cutting edge tactics and tools.
is currently the most advanced threat that the higher education community faces, against global adversaries who use cutting edge tactics and tools.
Accidental Cyber Threats
Finally, accidents and environmental factors can be the source of cyber threats to a university. Faculty, staff and students can cause accidental damage through lack of knowledge or training. Improperly handling data can lead to breaches just as damaging as those caused by criminal actors. Third parties can create a similar threat if they possess sensitive information as part of their contracted duties. Concerns over insider and third-party risk are not unique to higher education but, again, the comprehensive amount of student information that schools possess creates a large impact when such mistakes occur.
As part of their responsibility to increase the resilience of the higher education community, REN-ISAC is attempting to address these threats with the recent expansion and improvement of the services they offer.
Hopefully this list of threats provides a useful introduction to what higher education security professionals have to face on a daily basis. As part of their responsibility to increase the resilience of the higher education community, REN-ISAC is attempting to address these threats with the recent expansion and improvement of the services they offer. This is a more holistic view of threat management which acknowledges that pre-event threat awareness is the most efficient way to handle risk, that collaboration with stakeholders within and across sectors is vital to an effective sector response, and that cyber and physical risks are bleeding together like never before. Gate 15 is excited to be working with REN-ISAC on one of these growth initiatives: the Blended Threat Resilience Workshop Series. This series of workshops across the United States allows members of the higher education community, affiliated with REN-ISAC or not, to interact with their peers and discuss security issues, best practices, and other topics in order to strengthen the community’s overall resilience. This year, REN-ISAC also launched their Enterprise Participation Update, expanding the types of leaders and security positions that can become a part of their trusted communities model, as well as a Peer Assessment Service that provides evaluations of an institution’s cybersecurity posture by fellow cyber security practitioners from other schools. This is in addition to REN-ISAC’s best-in-class offerings to the higher education community, like Passive DNS scanning, the Daily Watch Report, and work on the Higher Education Cloud Vendor Assessment Tool (HECVAT). Overall, 2018 has been a very exciting year for REN-ISAC and its operations, and Gate 15 is proud and honored to be a part of that process!
See our previous posts on REN-ISAC and Higher Education Threats, Risks, and Preparedness:
- REN-ISAC: Higher Education Enterprise Risk Management Leadership, 06 Mar 2018
- Security Spotlight: An Interview with REN-ISAC Executive Director, Kim Milford, 11 Jun 2018
This blog was written by Brett Zupan, Gate 15 Risk Analyst.
 Brett Zupan is a Risk Analyst at Gate 15 with experience in all-hazards analysis, exercise development, and information sharing. He has supported analysis, preparedness and operations for a number of critical infrastructure communities, including support to Water and Wastewater Systems Sector, the Commercial Facilities Sector, and with Higher Education in support of REN-ISAC, among other projects. Before joining the company in 2016, he worked at the Georgia State Senate. Brett received his Masters of International Relations from American University.
Brett Zupan is a Risk Analyst at Gate 15 with experience in all-hazards analysis, exercise development, and information sharing. He has supported analysis, preparedness and operations for a number of critical infrastructure communities, including support to Water and Wastewater Systems Sector, the Commercial Facilities Sector, and with Higher Education in support of REN-ISAC, among other projects. Before joining the company in 2016, he worked at the Georgia State Senate. Brett received his Masters of International Relations from American University.
Maintain security and threat awareness via Gate 15’s free daily paper, the Gate 15 SUN and learn more about Hostile Events Preparedness and our HEPS Program here. Gate 15 provides intelligence and threat information to inform routine situational awareness, preparedness planning, and to penetrate the decision-making cycle to help inform time-sensitive decisions effecting operations, security, and resources. We provide clients with routine cyber and physical security products tailored to the individual client’s interests. Such products include relevant analysis, assessments, and mitigation strategies on a variety of topics.
here. Gate 15 provides intelligence and threat information to inform routine situational awareness, preparedness planning, and to penetrate the decision-making cycle to help inform time-sensitive decisions effecting operations, security, and resources. We provide clients with routine cyber and physical security products tailored to the individual client’s interests. Such products include relevant analysis, assessments, and mitigation strategies on a variety of topics.
Featured photo collage comprised of the images above and referenced below.
“People protest controversial Breitbart writer Milo Yiannopoulos at UC Berkeley on February 1. A scheduled speech by Yiannopoulos was canceled after the protests became violent.” Photo credit: Elijah Nouvelage/Getty via Newsweek, Inside the Black Bloc Protest Strategy That Shut Down Berkeley, 14 Feb 2017, https://www.newsweek.com/2017/02/24/berkeley-protest-milo-yiannopoulos-black-bloc-556264.html
Ohio State attack image, via WCPO Cincinnati, Names of 13 Ohio State attack victims released, 30 Nov 2016, https://www.wcpo.com/news/state/state-ohio/names-of-13-ohio-state-attack-victims-released
Chinese hackers wanted photo, from CNN, Chinese hackers infiltrated U.S. companies, attorney general says, 19 May 2014, https://www.cnn.com/2014/05/19/justice/china-hacking-charges/index.html
Uniaccount homepage image, via PhishLabs, Silent Librarian: More to the Story of the Iranian Mabna Institute Indictment, 26 Mar 2018, https://info.phishlabs.com/blog/silent-librarian-more-to-the-story-of-the-iranian-mabna-institute-indictment
