By David Pounder
To deliberately do anything means to carefully weight or consider; studied; intentional. When it comes to preparing for attack, this deliberate preparation can make a significant difference in the impact of the attack. This past week, the FBI released new documents pertaining to the Sandy Hook Elementary School massacre in which 26 people, including 20 children, were shot and killed by an attacker, who had also previously killed his mother to set off the chain of events. In the documents it was revealed that the attacker had planned this type of attack up to 21 months prior to the attack. The attacker had engaged online with an unidentified woman and revealed his fascination with school shootings and other mass murders, keeping a detailed spreadsheet of many of them. Additionally, he was very interested in school-aged children that could suggest he was a pedophile, though no evidence was gathered that he acted on it. In another set of documents, an unidentified man claimed the attacker revealed parts of his plan. This unidentified man informed local police prior to the attack but nothing was done.
The Hostile Events Attack Cycle details a process that attackers goes through when preparing for an attack. Whether they knowningly or unknowingly go through this process, elements of the 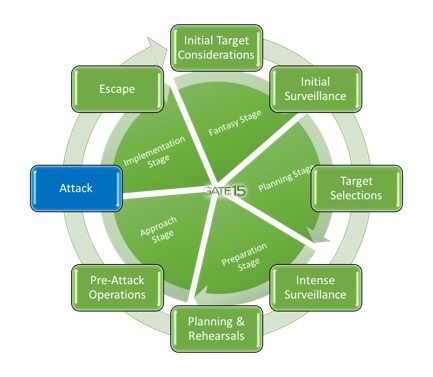 cycle are identified during the subsequent investigations and analysis of the event. The attack cycle begins with target selection and all the steps that go into identifying, surveilling, validating and ultimately confirming the target. It’s followed by attack planning steps which incorporate finalizing the plan, acquiring weapons and supplies needed to carry out and possibly escape from the attack, pre-attack checks to ensure everything is working as expected, and finally, rehearseals/walk throughs of the attack (which may be on a map, on a table with representations of the target and locations, or in their mind). Finally, they are ready for the attack, and possibly an escape. “Possibly” because some attacks are not designed for an escape. So for some attacks, the physical attack will be the last act, while in others, there will be an escape.
cycle are identified during the subsequent investigations and analysis of the event. The attack cycle begins with target selection and all the steps that go into identifying, surveilling, validating and ultimately confirming the target. It’s followed by attack planning steps which incorporate finalizing the plan, acquiring weapons and supplies needed to carry out and possibly escape from the attack, pre-attack checks to ensure everything is working as expected, and finally, rehearseals/walk throughs of the attack (which may be on a map, on a table with representations of the target and locations, or in their mind). Finally, they are ready for the attack, and possibly an escape. “Possibly” because some attacks are not designed for an escape. So for some attacks, the physical attack will be the last act, while in others, there will be an escape.
Another example of deliberate planning is evidenced through the Charleston, South Carolina Church shooting in 2015. Not only did the attacker do intenstive surveillance prior to the attack, but this was followed by detailed planning and reherseals that included firing his weapon and reloading it at various outdoor locations and his backyard. The attacker understood the target, visited the site, and even called it prior to the attack to confirm gathered information. He knew when a group was meeting because his discreet and open source surveillance had validated it, and he knew it was the oldest black church in the south. He carried 8 magazines with 11 rounds each, even though they could hold up to 13, so to ensure there were 88 rounds. The number 88 is a symbolic reference to Hitler. His original plan was to use a remaining round to commit suicide when the cops arrived, but since they did not come, he fled the scene and was on the run for 17 hours before being caught. This was part of the plan that failed him – he had no back up for suicide.
information. He knew when a group was meeting because his discreet and open source surveillance had validated it, and he knew it was the oldest black church in the south. He carried 8 magazines with 11 rounds each, even though they could hold up to 13, so to ensure there were 88 rounds. The number 88 is a symbolic reference to Hitler. His original plan was to use a remaining round to commit suicide when the cops arrived, but since they did not come, he fled the scene and was on the run for 17 hours before being caught. This was part of the plan that failed him – he had no back up for suicide.
Over the past month, more recent examples of attacks occurred show varying levels of planning and coordination.
In the Las Vegas concert shooting, the investigation to date shows that one man carefully planned and executed the most violent mass murder in US history resulting in the deaths of 58 people and injuring over 500 more. There are still many questions that need to be answered, with a motive still unknown, but it was clear that this was a carefully planned and orchestrated event. The attacker stockpiled weapons and ammunition, had calculated ranges, and is thought to have visited other venues around the country in what could be part of initial surveillance and target selection. Additionally, investigators examining the attacker’s computers found an “Internet search for techniques used by local police for breaching rooms in standoff situations. Investigators also discovered that a laptop belonging to Paddock is missing its hard drive, complicating efforts to uncover his motive….the Internet query and the missing hard drive, as well as the stockpiling of weapons and ammunition and staking out of concert venues in other U.S. cities, underscore Paddock’s meticulous preparation for the October 1 attack.” The investigation also claimed evidence was obtained that indicated the attacker may have planned an escape, and to survive for a period of time after the attack. It is possible the investigation will be able to confirm with certainty, but based on evidence in which the attacker blocked stairwells to frustrate first responders, an escape seemed unlikely, and may not have been fully understood by the attacker until the actual attack commenced.

On 14 October, at least 358 people were killed and over 300 hundred more were injured in what is one of the worst terrorist attacks in the world over the past several years in a Somalia truck bombing. A truck laden with military grade and homemade explosives detonated outside a hotel. The truck was stopped at a security checkpoint and was about to be searched before the driver crashed through the barriers and detonated the vehicle. The target was believed to be the Ministry of Foreign Affairs. For the driver, there most likely was not an escape plan, and especially when confronted with an enhanced security measure, but for the planners, they most likely remain in hiding and may not ever be identified. It is important to point out that while this attack still had devastating impacts, the attack planning may not have anticipated the security checkpoint, and could have potentially caused more destruction if it reached its intended target.
Workplace violence attacks also shows varying levels of planning. In a Maryland office shooting, an employee with a history of workplace violence, angry temperament, and criminal history, killed three employees and wounded two others at a small business in Maryland. The motivations of the attacker are still unclear, and while it does not appear to have been extensively planned, it does not seem to have been a random act either. Further evidence suggests that the attacker, perhaps understanding his pending fate, sought out another individual who he had quarreled with in the past in Delaware before being apprehended in a nearby town. While this incident appears to have been triggered by a situation or circumstance, the San Bernardino 2015 attack is an example of a workplace attack / active shooter scenario that was well planned and included an escape plan. The investigation into the attack that killed 14 and wounded 22 showed that the attackers had planned various types of attacks as far back as 2011, and could have been worse if left behind bombs would have detonated as designed.
With every attack, there is some culmination. The attacker could plan to give their life for their cause, while others can attempt to flee, or die trying to escape. Some of the reasons that make escapes a challenge for the attacker results from the extra planning, coordination and logistics required, and anticipating the security response, which is not something that can easily be planned or understood. What makes an attack successful is the level of planning and preparedness, as well as the element of surprise. The attacker intends to catch the target at its most vulnerable time, as was the case in the May 2017 Manchester Arena bombing. However, what an attacker cannot completely plan for is the response from first responders, security elements, or eyewitnesses. An attacker can conceivably have a plan for escape but can’t very easily conduct a rehearsal realistically replicating similar conditions, or events. In the Boston Marathon bombing, the attackers fled the scene with the intent of additional attacks, ultimately carjacked a car and setting off a scene they could not have planned or anticipated which led to one attackers death and the subsequent arrest of the other.
Another immeasurable factor in planning an escape is the adrenaline rush that accompanies an attack. The attacker has just completed an attack and is on an emotional high and gets a big adrenaline spike. However, if not trained for, this can spike can result in mistakes. According to Psychology Today, “With a big hit of adrenaline, we tend to lose situational awareness. Our brains perceive danger and prepare us for ‘fight or flight.’ We lose our peripheral vision and focus on what is right in front of us. Our brain works to filter out any sound extraneous to the direct threat (auditory exclusion). We hyperventilate or hold our breaths. In some instances, this is exactly what we need to get out of harm’s way, but in many intense situations, we need to be able to think clearly, hear what people around us are saying, breathe deeply to send oxygen to our brains, and act effectively to be able to survive the situation or master the skill we are learning.” With this in mind, even the most well-planned escape and evasion could be derailed simply through the adrenaline rush that accompanies the attack.
However, in many instances, escapes are not part of the plan, or death is viewed as the final escape, and is never a consideration as part of the attack. Depending on the attacker’s moral, ethical, or religious views, death may be viewed as the ultimate achievement in support of their beliefs and cause. And in other situations, such as workplace violence murder-suicides, death may be the escape from events in their life or that pre-empted the violence.
Not all attacks go through these levels of planning and preparedness, and some unfortunately are simply random acts of violence. However, understanding and recognizing the varying degrees, as well as the Hostile Events Attack Cycle at large, can help organiztions plan and prepare their own security counter-measures and defenses.
Maintain security and threat awareness via Gate 15’s free daily paper, the Gate 15 SUN and learn more about Hostile Events Preparedness and our HEPS Program here. Gate 15 provides intelligence and threat information to inform routine situational awareness, preparedness planning, and to penetrate the decision-making cycle to help inform time-sensitive decisions effecting operations, security, and resources. We provide clients with routine cyber and physical security products tailored to the individual client’s interests. Such products include relevant analysis, assessments, and mitigation strategies on a variety of topics.
provides intelligence and threat information to inform routine situational awareness, preparedness planning, and to penetrate the decision-making cycle to help inform time-sensitive decisions effecting operations, security, and resources. We provide clients with routine cyber and physical security products tailored to the individual client’s interests. Such products include relevant analysis, assessments, and mitigation strategies on a variety of topics.
 This blog post was written by David pounder, a Gate 15 Senior Risk Analyst for Intelligence and Analysis. Dave provides expert threat and risk analysis, assessments and special project support for internal activities and client needs.
This blog post was written by David pounder, a Gate 15 Senior Risk Analyst for Intelligence and Analysis. Dave provides expert threat and risk analysis, assessments and special project support for internal activities and client needs.
Featured image, “Remembering Sandy Hook, via NBC New York, 14 Dec 2015, https://www.nbcnewyork.com/news/national-international/Complete-Coverage-of-Connecticut-Elementary-School-Massacre-183534881.html
