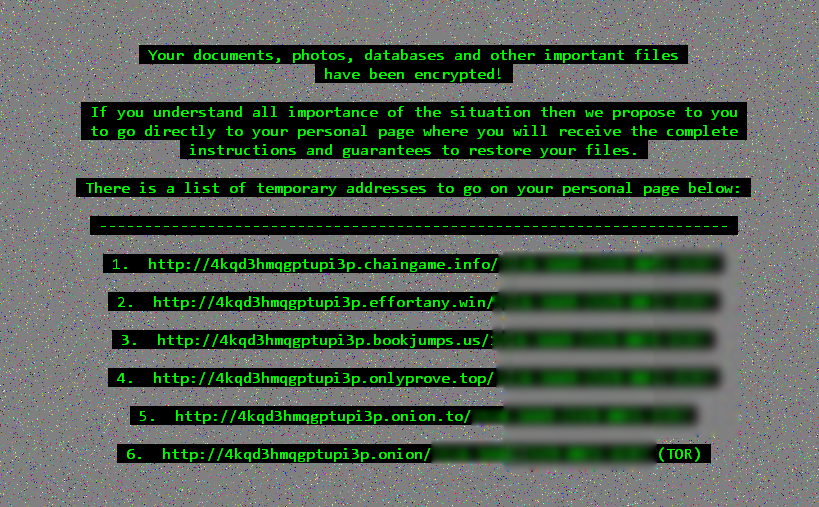
Recently, two Gate 15 team members – Kristi Horton, Senior Risk Analyst in Cybersecurity, and Chip Wickenden, Director of Strategic Relationships, had a conversation about ransomware and different kinds of threat actors that took some interesting turns. We captured that dialogue here to share their insights.
Chip: Hi Kristi, during a recent ransomware briefing, I had a very unsettling thought. As the field of cybersecurity has progressed, banks have traditionally been the most popular target for cyberattacks, since that’s where the money is. But as they have hardened their security posture, crooks have expanded to other targets, like healthcare, transportation – really, across the critical infrastructure community – and now we’re seeing indications of increasing interest in Industrial Control Systems (ICS). At the same time, crooks have discovered ransomware and also built relationships with state actors. It seems like the combination of growing ransomware development and the growth of non-financial targets could result in “weaponized ransomware.”
 Kristi: I think that follows a plausible progression. I’m wondering what “weaponized” ransomware would look like. How would it be different from ransomware?
Kristi: I think that follows a plausible progression. I’m wondering what “weaponized” ransomware would look like. How would it be different from ransomware?
Chip: Ransomware does damage today in order to extract financial gain, so in a sense it’s already weaponized. I guess I’m concerned about it in the hands of politically-motivated bad guys.
Kristi: I wouldn’t be surprised if a few nation-states known to engage in criminal activity were not already benefitting from ransomware. One state in particular is broke and known to engage in all forms of petty and felonious crimes to raise money. It’s important, however, to remember that not all crooks are the same. Cybercriminals that attack banks are motivated by financial gain; terrorists and nation-states tend to have more political motivations.
The difference between nation-states and sophisticated criminal groups is getting harder to discern as some states are using criminals to achieve their objectives. Some criminal groups are as sophisticated and well-funded as nation-states…
Chip: I probably over simplified. As the trend towards ICS ransomware grows, the attack vector to ICS creates a means for state actors to create kinetic damage, instead of getting rich. I think the same holds true for transportation and healthcare. So are the crooks making money doing R&D for state actors?
Kristi: That’s already happening, just not necessarily with ransomware.
Chip: Right – but I’m concerned that ransomware will accelerate the trend, since it injects more money into the creative drive to find new vectors.
As you pointed out, the term “crooks” can cover a lot of ground, so let me zero in on malware developers and their customers; the people that buy tools from them, either for illegal economic gain (criminals), or for political purposes, either nation states or terrorist groups.
Kristi: I see ransomware as a tool like any other tool. They might use it, they might not, but I don’t think it empowers adversaries more than other tools at their disposal. Those with the most motivation to cause kinetic harm that could result in loss of life or injury are less likely to be nation states and more along the lines of terrorist groups.
I am watching to see signals that aggressive non-state actors who want to rule are financially benefitting from ransomware. Some are certainly benefitting from the drug trade and other illicit activities.
It wouldn’t shock me at all to learn that the supply chain available for ransomware had empowered a faster shift toward cyber fundraising. Tactically, I’m also concerned that the proceeds of ransomware may be funding terrorist activity. That’s something that needs to be looked at.
Chip: I think we agree on all of these points. I’m thinking farther up the crooks’ supply chain to the R&D that goes into ransomware. As it focuses more on ICS, transportation, healthcare, and other non-financial areas, the bad guys’ researchers identify more vectors faster that can cause kinetic damage. So the acceleration of ransomware could create, as a byproduct, an acceleration of attacks in these targeted areas as acts of war.
Kristi: We have to hope the bug bounty programs, which seem to be expanding and getting more support, will reveal the vulnerabilities faster than R&D. The criminal R&D work is driven by different motives than the nation-state R&D. They both do it. Criminals are usually reticent to cause kinetic damage unless the client can shield them from the consequences of extradition or assassination.
There has been a symbiotic relationship between criminal groups and nation-states for decades and certainly before computers were invented; the ability to take down systems that save lives has existed long before ransomware.
Many miscreants are driven by a natural curiosity and pride that they can do harmful things, they might even do a proof-of-concept, but they also do not want to be caught or interrupted. That’s often what drives the developer. Criminals, who are responsible for the majority of cyber incidents, are really just in it for the money, but we are seeing more activity from politically motivated actors.
The more sophisticated criminal groups won’t participate in things that really cause kinetic harm because they don’t want the consequences. Keep in mind that while the United States may not kill them, the government would extradite them.
This is not true for other countries targeted by the nation-state clients of crimeware rings. Some countries, after being targeted, will seek to apprehend them “Dead or Alive,” especially if their work results in death of citizens. Other countries will just “shoot back.”
Outside of the US, the US is still seen as the cyber superpower; we are seen as the top threat to other nation-states, businesses, and individuals. The US is still a military superpower and still has the most sophisticated law enforcement investigation methods. The US is asked by allies (and adversaries for that matter) to help investigate when they are attacked.
Given that, the consequences of attacking the US in ways that result in the loss of human life is a very serious proposition. Many criminal groups won’t think twice about robbing us blind or defacing websites, but they do not want to face the consequences of killing Americans, even accidentally.
Chip: Wow – this sheds a lot of light. Thank you! So to summarize, do you think that reticence to “cross the line” could actually be seen as a key driver for crooks to actually honor ransom p ayments?
ayments?
Kristi: I see the driver to honor ransomware payments to be in the interest of criminals – as “more money;” if people do not trust that they will regain access to data and devices, they will stop paying ransoms. Further, many criminals only hesitate when human life or safety is at risk. They never seem to have a problem with any other activities. They don’t mind disruption, vandalism, theft, or harm to networks or systems. Some draw the line because that is where their personal convictions are, most do it because they fear the consequences of harming humans.
There is a ton of literature on this in the fields of sociology and psychology and especially in criminology. A lot of the same observations about criminal behavior prior to cyber crime hold for cyber criminals, too. The few areas where they differed were very interesting, too.
Another countervailing trend is that consortiums of cryptographers – such as nomoreransom.org – private sector and government professionals who identify and publish keys and tools to decrypt data are disrupting the ransomware business model as well. More ways are being found for victims to get their data back for free. We should note that the FBI recommends that victims should never pay criminals in ransomware attacks and that attacks should be reported to the FBI and other regulatory and law enforcement agencies as appropriate.