By Andy Jabbour
In Brief: Security, preparedness, and resilience – whether focused on terrorism, health risks, natural hazards, cybersecurity, or any number of other concerns – require good partners and professionals that strive to achieve effective coordination with other organizations and to help colleagues and organizations maintain awareness of threats, risks and other relevant information. The following is an example of where the team at Farsight Security did that very thoughtfully and well in regards to one systemic threat to the Internet – the design and implementation of the DNS Internationalized Domain Name (IDN) system.
Internationalized Domain Name (IDN) system.
Read Farsight’s blog: “Touched by an IDN: Farsight Security shines a light on the Internet’s oft-ignored and undetected security problem,” (17 Jan 2018) to gain a deeper dive into this threat. The blog was written, “to bridge that knowledge gap – to offer a keyhole glimpse into the shadowy world of brand lookalike abuse via IDN homographs.”
Is your security team building trusted relationships with professional peers, networks, and organizations? In an ever-increasing blended threat environment, our collective defense and effective collaboration are more important than ever.
Now, if you have more than a thirty second attention span… read on!
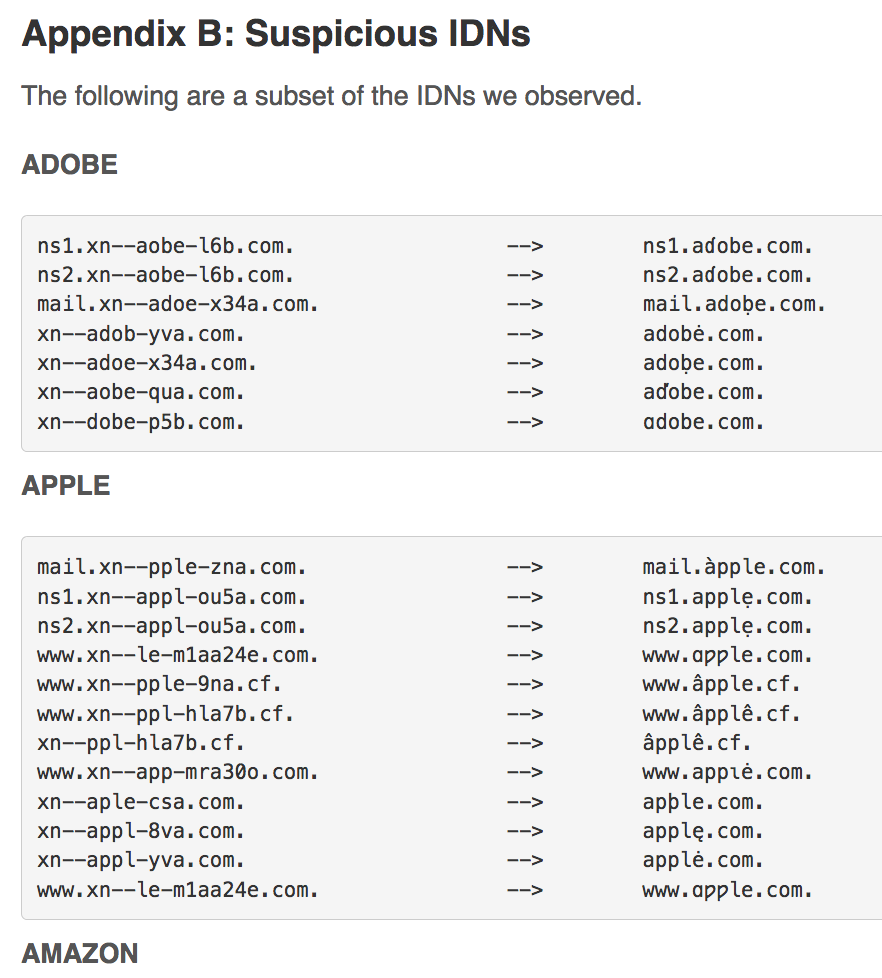
This image from the Farsight Security blog, “Touched by an IDN: Farsight Security shines a light on the Internet’s oft-ignored and undetected security problem,” 17 Jan 2018
There are a number of examples where silos have frustrated effective intra-organizational coordination, or where something has been publicly posted without informing individuals or organizations that may not appreciate what is being told to the world, or any number of stories where poor coordination caused frustration – sometimes annoyingly, sometimes dangerously. But (!) there are good stories too! And this post is about one of those. While this post is regarding a cybersecurity issue, the example of outreach and collaboration are much more broadly relevant across security, preparedness, and resilience – regardless of the domain or main focus.
As part of their commitment “to making online interactions safer for all users, Farsight Security regularly investigates systemic threats to the Internet.” In that spirit, they took time to dive into the design and implementation of the DNS Internationalized Domain Name (IDN) system. In doing so, Farsight identified some concerns regarding “the prevalence and reach of homographs, in the form of IDN lookalike domains, across the Internet. Specifically, Farsight examined 125 top brand domain names, including large content providers, social networking giants, financial websites, luxury brands, cryptocurrency exchanges and other popular websites… the potential security risk posed by IDN homographs is significant.”
“Specifically, Farsight examined 125 top brand domain names, including large content providers, social networking giants, financial websites, luxury brands… the potential security risk posed by IDN homographs is significant.”
Identifying risks relating to many of those “125 top brand domain names,” Farsight sought to reach out to each organization individually (well ahead of publishing their findings) to respectfully inform them, one-on-one, of the issue in order to let those organizations get ahead of any concerns they may have or any inquiries they may receive. In that effort, they reached out via publicly available contact information and known POCs, with some success and some dead ends. Not being content there, they reached out to colleagues and other security professionals to get help identifying appropriate contacts to speak with.
It was in that effort that our team connected with Paul Vixie, Chairman and CEO at Farsight Security. Now, Paul is one of those really, really smart guys. Hearing him present at Anomali Detect last year, the colleague I was there with said it was like hearing Yoda speak. Well, if Paul is Yoda, while I’d love to say I’m Luke, I’m not. Remember the scene in Episode 6 when the Ewoks are defending Endor from the Empire? If Paul is Yoda-like (no, I’m not even an Ewok), I’m like one of the logs the Ewoks used to slam into the attacking Walkers…
Security – across all domains, physically nearby or across the expanse of cyberspace – should be done in a spirit of collaboration and respect. When the good guys work together, the good guys win. From time-to-time, it is good to pause and consider your relationships.
Our team works with a variety of partners, including some amazing critical infrastructure partners in the community of Information Sharing and Analysis Centers (ISACs). As Paul was  trying to connect with members of one of those communities, we were able to reach out to one ISAC’s leadership team, who were then able to connect us to one of the implicated companies’ leads for risk management. That contact connected his security team with Farsight Security. Contact made. Information shared. That was completed a week before the blog posted, allowing the company time to do whatever they wanted to ahead of publication.
trying to connect with members of one of those communities, we were able to reach out to one ISAC’s leadership team, who were then able to connect us to one of the implicated companies’ leads for risk management. That contact connected his security team with Farsight Security. Contact made. Information shared. That was completed a week before the blog posted, allowing the company time to do whatever they wanted to ahead of publication.
Farsight could have gone about this very differently. They could have made this appear negative for the listed companies, or just posted it without spending time (by their CEO…) to try and identify contacts to inform. But they didn’t. They did it right. They did it responsibly and professionally.
Security – across all domains, physically nearby or across the expanse of cyberspace – should be done in a spirit of collaboration and respect. When the good guys work together, the good guys win. From time-to-time, it is good to pause and consider your relationships. Do you know your facility’s neighboring security leaders? Are you connected with local law enforcement, fusion centers, and homeland security contacts? Are you a member of your Sector’s ISAC? Is your security team building trusted relationships with professional peers, networks, and organizations? In an ever increasing blended threat environment, our collective defense and effective collaboration are more important than ever.
About Farsight Security: “Farsight Security provides the world’s largest real-time actionable threat intelligence on how the Internet is changing. Leveraging proprietary technology purpose-built to manage volumes of data and real-time analysis, Farsight observes over 200,000 DNS resolutions per second.”
This blog was written by Andy Jabbour, Gate 15’s Co-Founder and Managing Director. Andy leads Gate 15’s risk management and critical infrastructure operations with focus on Information Sharing, Threat Analysis, Operational Support & Preparedness Activities (Planning, Training & Exercise). Andy has years of experience working with partners across the critical infrastructure and homeland security enterprise to support national security and client business needs.
Maintain security and threat awareness via Gate 15’s free daily paper, the Gate 15 SUN and learn more about Hostile Events Preparedness and our HEPS Program here. Gate 15 provides intelligence and threat information to inform routine situational awareness, preparedness planning, and to penetrate the decision-making cycle to help inform time-sensitive decisions effecting operations, security, and resources. We provide clients with routine cyber and physical security products tailored to the individual client’s interests. Such products include relevant analysis, assessments, and mitigation strategies on a variety of topics.
routine situational awareness, preparedness planning, and to penetrate the decision-making cycle to help inform time-sensitive decisions effecting operations, security, and resources. We provide clients with routine cyber and physical security products tailored to the individual client’s interests. Such products include relevant analysis, assessments, and mitigation strategies on a variety of topics.
