“If you don’t immediately stop the clearing of the Hambach Forest, we will attack your servers and bring down your web pages, causing you economic damage that you will never recover from…”
 This blog has routinely featured posts addressing the idea of blended threats. As we continue two ongoing series of exercises around the United States that have been focused on current threats and emerging risks to critical infrastructure, we’ve often discussed the idea of complex and blended threats. And, though as a society we seem to be decreasing our emphasis on vocabulary and effective use of language for emojis, hashtags, and soundbites, it’s important that from a threat and risk perspective, we properly understand and refer to what we mean to speak to.
This blog has routinely featured posts addressing the idea of blended threats. As we continue two ongoing series of exercises around the United States that have been focused on current threats and emerging risks to critical infrastructure, we’ve often discussed the idea of complex and blended threats. And, though as a society we seem to be decreasing our emphasis on vocabulary and effective use of language for emojis, hashtags, and soundbites, it’s important that from a threat and risk perspective, we properly understand and refer to what we mean to speak to.
When we disagree about the proper pronunciation of potatoes, we’re obviously still discussing “an erect South American herb of the nightshade family widely cultivated for its edible starchy tuber” (Merriam-Webster’s simple definition!) but if we’re discussing potatoes and tomatoes, we’re talking about two different foods altogether, one of which I’m never quite sure whether it’s a fruit or vegetable…
When talking vegetables, both potatoes and tomatoes can be served up in numerous, delicious ways. And when talking threats, both complex and blended threats can be contrived in ways to make attackers salivate.
Working with colleagues and through our own refinement, we’ve defined blended threats as natural, accidental, or purposeful physical or cyber dangers that have or indicate the potential to have crossover impacts and harm life, information, operations, the environment, and/or property.
A key distinction of blended threats is the above noted crossover component – one attack, with crossover effects. What we mean by crossover is a threat the originates in one domain (say cyber or natural hazard) and that has impacts across to another domain (say physical infrastructure or network capabilities). That is different than complex threats.
A key distinction of blended threats is the crossover component – one attack, with crossover effects; a threat that originates in one domain and that has impacts across to another domain
Complex threats would be two or more separate attacks aimed at the same general or specific target(s) or objective(s). Complex attacks could be multiple attacks of one kind – say hostile events aimed at a specific series of targets as seen in the Paris terrorist attacks in 2015 – or they could be, for example, something involving both a cyberattack and a separate physical activity, that may or may not be coordinated efforts.
Examples of complex threats can be seen in examples such as some of Anonymous supporters’ past activities, where there have been mass protests and related cyberattacks. More recently and more directly focused, this can be observed in a story coming from Germany, where physical protests were held as a cyberattack – in this case a DDoS – was also conducted. It is not known whether the separate activities were in any way coordinated. From Deutsche Welle, 25 Sep 2018:
German company RWE filed a police complaint against unknown attackers who had targeted RWE’s public website, a company representative said. The firm’s webpage was flooded with distributed denial-of-service (DDoS) attacks and remained virtually  inaccessible by Tuesday morning. The company said that no other systems had been attacked. RWE currently faces harsh criticism from environmental groupsover its plans to expand coal mining operations by clearing the ancient Hambach Forest. The scheme has been held up by protesters blocking the site. Police started clearing away the activists earlier this month, but the widely publicized removals were briefly suspended after a journalist fell to his death. On Monday, the evictions resumed. The mass-circulation daily Bild linked the attack with a Youtube video using the symbols of the hacker group Anonymous. The German-language clip, posted last week by Anonymous Deutsch, calls on RWE to ‘keep your hands away from the Hambach Forest.’ ‘If you don’t immediately stop the clearing of the Hambach Forest, we will attack your servers and bring down your web pages, causing you economic damage that you will never recover from,’ says the computer-generated voice in the video. ‘Together, we will bring RWE to its knees,’ it adds, calling the viewers to boycott the company. ‘This is our first and last warning.’
inaccessible by Tuesday morning. The company said that no other systems had been attacked. RWE currently faces harsh criticism from environmental groupsover its plans to expand coal mining operations by clearing the ancient Hambach Forest. The scheme has been held up by protesters blocking the site. Police started clearing away the activists earlier this month, but the widely publicized removals were briefly suspended after a journalist fell to his death. On Monday, the evictions resumed. The mass-circulation daily Bild linked the attack with a Youtube video using the symbols of the hacker group Anonymous. The German-language clip, posted last week by Anonymous Deutsch, calls on RWE to ‘keep your hands away from the Hambach Forest.’ ‘If you don’t immediately stop the clearing of the Hambach Forest, we will attack your servers and bring down your web pages, causing you economic damage that you will never recover from,’ says the computer-generated voice in the video. ‘Together, we will bring RWE to its knees,’ it adds, calling the viewers to boycott the company. ‘This is our first and last warning.’
This is a timely example of a complex threat, with a two-pronged attack on different domains with physical protests and network attacks. A blended threat would have been something involving one attack – say a cyberattack aimed at RWE – that was somehow able to disable physical infrastructure.
Blended attacks and complex attacks are distinct from one another, though there could be complex, blended attacks involving, for example, physical protests or vandalism, coupled with cyberattacks impacting physical systems. Imagine a well-planned and coordinated mass protest across multiple major cities worldwide, featuring the seemingly ever-present black bloc protests of the Pacific Northwest and physical altercations in various locations, or inspired bombing attempts such as the one disrupted in Cleveland in 2012 during planned May Day demonstrations by Occupy Cleveland, combined with a cyberattack that disrupted transportation systems in those same protest cities. In this case, we’d have physical security events and the associated threats and risks those bring, coupled with a blended attack on infrastructure, combining into what could be significant disruption delivered in a coordinated, complex, blended attack. That’s a mouthful.
complex, blended attacks involving, for example, physical protests or vandalism, coupled with cyberattacks impacting physical systems. Imagine a well-planned and coordinated mass protest across multiple major cities worldwide, featuring the seemingly ever-present black bloc protests of the Pacific Northwest and physical altercations in various locations, or inspired bombing attempts such as the one disrupted in Cleveland in 2012 during planned May Day demonstrations by Occupy Cleveland, combined with a cyberattack that disrupted transportation systems in those same protest cities. In this case, we’d have physical security events and the associated threats and risks those bring, coupled with a blended attack on infrastructure, combining into what could be significant disruption delivered in a coordinated, complex, blended attack. That’s a mouthful.
“Imagine a well-planned and coordinated mass protest across multiple major cities (with) physical altercations in various locations, combined with a cyberattack that disrupted transportation systems in those same protest cities…”
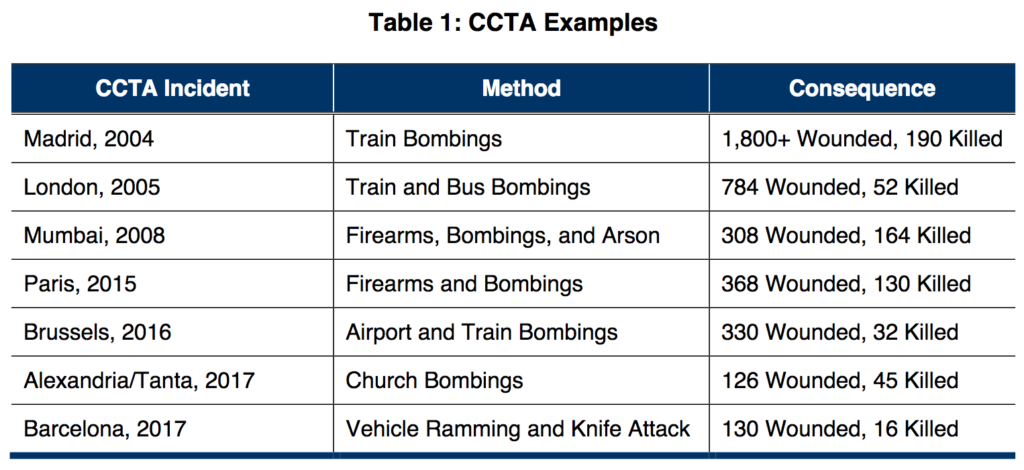
This image, from FEMA: Planning Considerations: Complex Coordinated Terrorist Attack, https://www.fema.gov/media-library/assets/documents/167777 and PDF: https://www.fema.gov/media-library-data/1532550673102-c4846f270150682decbda99b37524ca6/Planning_Considerations-Complex_Coordinated_Terrorist_Attacks.pdf (page 2)
Perhaps more concerning would be a planned complex coordinated terrorist attack – not unlike what Paris experienced in 2015 when multiple attackers, armed with assault rifles and explosives, targeted six locations across Paris, killing 130 and wounding over 400 more – but with the added complexity of attackers purposefully disrupting communications in the attack areas to frustrate evacuations and response. Here, we’d have hostile events enhanced by cyberattacks on physical infrastructure. If the communications attacks were purely cyber, this would be a complex attack. If the communications attacks were somehow able to affect the physical infrastructure supporting communications, that would be a blended attack.
Complex attacks are the more likely threat organizations face today, and the German protests activities serve as a real example of how those can develop and be conducted. Blended threats, for the most part, are still an emerging threat (though there are notable instances of blended attacks – such as Stuxnet, Triton / Trisis, and Industoyer). While some sectors of critical infrastructure are more prone to those attacks now than others, blended threats are a reality we have to increasingly consider as we implement new technology into our critical infrastructure – from our buildings and venues, to our critical lifelines, and in the vital services on which we depend.
Our team includes security updates in our free daily paper, the Gate 15 SUN. We encourage readers to consider the evolving blended threat environment and to take that into consideration as you plan and conduct preparedness, security and operations. Read some of our previous posts on blended threats in the links below.
- Blended Threats! McAfee Labs Addresses Digital Impacts to Physical Infrastructure
- Blended Threats: Mining Takes a Toll!
- Blended Threats (update 1.1): Understanding an Evolving Threat Environment
- Blended Threats: The Oracle Has Spoken!
- More on blended threats, some of our associated preparedness activities, and other content that may be of interest can be accessed from our blog.
Understand the Threats. Assess the Risks. Take Action.
What are blended threats? A blended threat is a natural, accidental, or purposeful physical or cyber danger that has or indicates the potential to have crossover impacts and harm life, information, operations, the environment, and/or property.
References:
There are a number of hyperlinks in the post above. Highlighted and additional references include:
- Featured image via Hambacher Forst: Hacker legen RWE-Website lahm – 50 Baumhäuser geräumt, Watson, 25 Sep 2018, https://www.watson.de/deutschland/nrw/936166582-hambacher-forst-hacker-legen-rwe-website-lahm-polizei-hat-schon-50-baumhaeuser-geraeumt
- Hackers attack RWE website amid Hambach Forest evictions, DW, 25 Sep 2018, https://www.dw.com/en/hackers-attack-rwe-website-amid-hambach-forest-evictions/a-45624149
- FDA warns users of cyber vulnerability in pacemaker programmers, CyberScoop, 12 Oct 2018, https://www.cyberscoop.com/medtronic-programmers-fda-cybersecurity-advisory/
- Jeep hackers at it again, this time taking control of steering and braking systems, The Verge, 02 Aug 2016, https://www.theverge.com/2016/8/2/12353186/car-hack-jeep-cherokee-vulnerability-miller-valasek
Maintain security and threat awareness via Gate 15’s free daily paper, the Gate 15 SUN and learn more about Hostile Events Preparedness and our HEPS Program here. Gate 15 provides intelligence and threat information to inform  routine situational awareness, preparedness planning, and to penetrate the decision-making cycle to help inform time-sensitive decisions effecting operations, security, and resources. We provide clients with routine cyber and physical security products tailored to the individual client’s interests. Such products include relevant analysis, assessments, and mitigation strategies on a variety of topics.
routine situational awareness, preparedness planning, and to penetrate the decision-making cycle to help inform time-sensitive decisions effecting operations, security, and resources. We provide clients with routine cyber and physical security products tailored to the individual client’s interests. Such products include relevant analysis, assessments, and mitigation strategies on a variety of topics.
