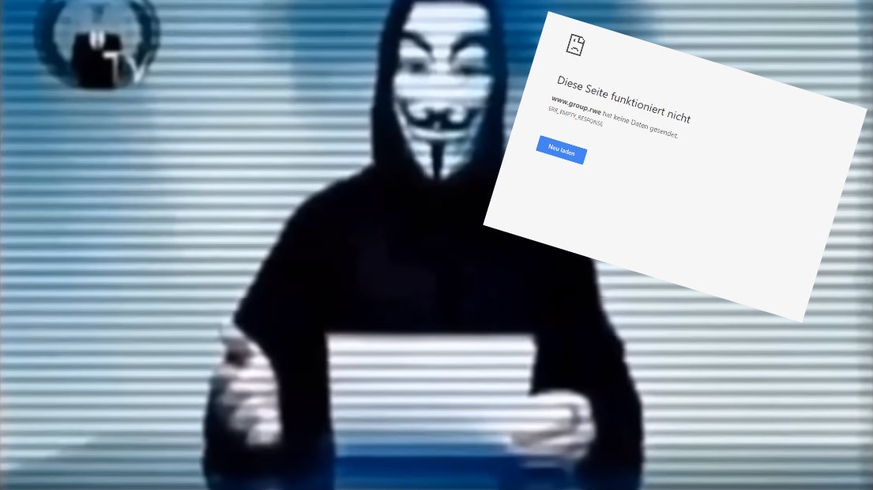
“If you don’t immediately stop the clearing of the Hambach Forest, we will attack your servers and bring down your…
by Andy Jabbour Seemingly every day a new data breach is reported, a new cybercrime effort is launched, fraud and extortion…
“Cyberattacks have always been, well, cyber. Their immediate effects were on our data, our digital information, and our devices…until they…
A new report from the Cyber Threat Alliance (CTA) highlights one type of blended threat that organizations should be aware…
Sean Lyngaas, @snlyngaas, writing in CyberScoop last week, wrote, “When it comes to protecting faith-based organizations from hackers, divine intervention will…
US critical infrastructure, most recently defined in President Obama’s 2013 Presidential Policy Directive 21 (PPD-21): Critical Infrastructure Security and Resilience,…
In this blog, we’ve written a few times about the idea of “Blended Threats,” and some of the ways the…
By David Pounder This is the third and final part of an ongoing series focused on the Hostile Events Attack…
By Bridget Johnson (@BridgetCJ) Much of the action at Saturday’s Unite the Right rally in Washington took place off…
By Brett Zupan There is a tremendous amount of information that analysts, security and risk leaders, executives, and others…
By David Pounder This is the second part of an ongoing series focused on the Hostile Events Attack Cycle. Previously…
In a recent post introducing the preparedness efforts that the National Health Information Sharing and Analysis Center (NH-ISAC) is taking to…
By David Pounder Threats operate in all shapes and sizes, and whether by design or not they tend to follow…
A recent post introduced the preparedness efforts that the Research and Education Network Information Sharing and Analysis Center (REN-ISAC) is taking…
It is rare that the US Government asks everyone to do something, and it can be challenging to get that…
By David Pounder On 14 February, a former student entered Stoneman Douglass High School in Parkland, Florida and killed…
By Brett Zupan and Andy Jabbour Across critical infrastructure, organizations must continually reassess their risks based on an ever-changing…
By Andy Jabbour This is an update to the original post, “Terminology for $500. What Are Blended Attacks?” 26 May…
By Andy Jabbour In Brief: On 22 Feb, President Trump made remarks regarding the 14 Feb mass shooting at…
By Bridget Johnson (@BridgetCJ) Not to be outdone by the Kurdish, Arabic and Assyrian women who have kicked their…
By Andy Jabbour There is a tremendous amount of information that analysts, security and risk leaders, executives, and others…
By Andy Jabbour Please note, this post has been updated to reflect the changes posted in update 1.1, 01 Mar…
By Andy Jabbour In Brief: Security, preparedness, and resilience – whether focused on terrorism, health risks, natural hazards, cybersecurity,…
By Bridget Johnson (@BridgetCJ) The Department of Homeland Security rang in the holiday season by adding a new office to…
By Bridget Johnson (@BridgetCJ) A pre-Christmas attack-plot arrest and shooting spree targeting police officers unfolded on different sides of the country…
By Bridget Johnson (@BridgetCJ) After a lull in post-Charlottesville white nationalist protests and counter-demonstrations, the nighttime 20 Dec. removal of…
By Bridget Johnson (@BridgetCJ) Wildfires that have been chewing through Southern California, with not much relief currently in sight from…
By Andy Jabbour Following the House of Representatives, the US Senate needs to approve the re-designation of DHS’s National…
By Bridget Johnson (@BridgetCJ) Maybe the Islamic State is starting to consider the usefulness of the al-Qaeda job application…
By Bridget Johnson (whose Twitter account remains suspended due to Twitter’s inexplicable policies and enforcement, and inability to respond in a…